5th European Conference: sustainable and innovative public procurement Read more
GDPR Organizational Technical Measure – What now?
Companies also have to gain from applying the key measures provided by the General Data Protection Regulation. This is what Bruno Rodrigues, from APDPO, explains to us.
Since the entry into force of the General Data Protection Regulation (GDPR), there have been many questions concerning the technical adequacy of the organizations to comply with them.
If on the one hand there are European organizations that far exceed the security imposed by the GDPR, on the other hand, and in most Portuguese SMEs, the evolution of IT Security and data protection is generally very low.
Since this evolution, which is expensive in terms of working hours and financial resources, is highly recommended and welcomed for the sake of data protection of the company and its information systems, I present some generic recommendations on how to approach the problem.
1 – GDPR technical view from the State perspective
With the entry into force of the GDPR, it was not long before the current Government published in its opinion, and in a generic way, what technical areas the entire public administration should give its attention? This is undoubtedly an important step for private organizations since, as I understand it, it will help companies choose which areas require immediate intervention from the point of view of Data Security, thus, with private entities conforming in the same degree as public entities.
It should be noted that compliance does not in any way mean that the organization is effectively safe. It is, however, a good start. To do this, just consult the Resolution of the Council of Ministers no. 41/2018.
This resolution distinguishes three layers of action, of extreme importance – Front-End, Application and Database. These three layers, from a security processes perspective, are included in a subject called IT Security Governance.
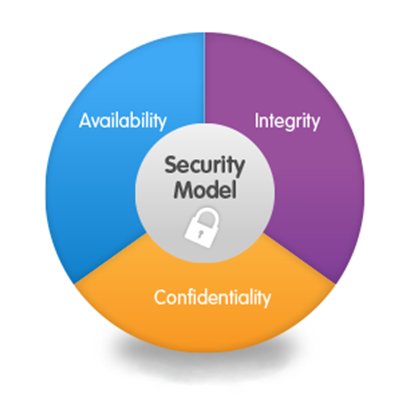
2 – CID – Confidentiality, Integrity and Availability
One of the pillars of Computer Security is the CIA (Confidentiality, Integrity & Availability). Used since the beginning of computer networks, it serves to provide organizations with three fundamental concepts of computer security that should be applied to its fullest to all situations of organizations, including data protection:
- Confidentiality – It means that the data is stored in a secure way and only accessible to authorized persons or processes. Simply put, it means that we protect data from unauthorized access;
- Integrity – Protection of data against unauthorized modification, loss, theft and unauthorized disclosure;
- Availability – Systems must guarantee redundancy and availability, and there should not be a “single point of failure”.
3 – The software Security Development Lifecycle
One of the focuses of the Council of Ministers resolution is on software scenario. This is one of the most important issues in the current computer security landscape and much could be written on the subject.
I want to make an introduction to the topic by mentioning a tool, which being limited, can greatly help Data Protection Officers work with development teams in data protection – https://www.microsoft.com/en-us/SDL .
In addition to the various “guides” available on this page and others (I always advise to consult the OWASP on the subject), Microsoft has developed a software that will allow organizations to quickly understand which attacks to take into account in the software development process.
At each stage of the process, in the various components and in projects ranging from a simple site to a complete ERP systems, the organization, even in projects developed by external entities, must have an understanding of the various attacks that can potentially compromise personal data as well as, what measures are being implemented to mitigate them.
Data and organization security aims to protect users, their customers and stakeholders from potential attacks and loss of information and should always be seen in layers, where technical measures should target the CIA’s assurance in all the company areas.
More in Communication
- Public Protection
- law firm
- BAS
- Covid-19
- 10 years
- anniversary
- Best Lawyers
- Portugal
- Who's Who
- Video surveillance
- Privacy
- Minors
- Health and Sciences
- Public Policies
- Coronavírus
- Atividade
- Real Estate 2020
- Corporate Law
- Legal Persons
- Companies
- Professional Secret
- Confidentiality
- Changes
- Public Law
- Life Sciences
- Awards
- Labour Awards
- Law
- Exceptional Measures
- State Budget
- Contracts
- Iberian Lawyers
- Lay-Off
- Lay-Off
- Mental Health
- Stress
- Saúde mental
- Leaders League
- Actualidade Ibérica
- Almedina
- Idealista
- APMEP
- Congress
- MIPIM
- SIGI
- REIT
- Imobiliário
- Mozambique
- ICLG
- Moçambique
- Secrecy
- Professional secrecy
- Labor
- ILO
- International Labor Organization
- RCBE
- sociedades
- pessoas coletivas
- Expo Real
- National Health Service
- NHS
- Hospitals
- Book
- PhD thesis
- Schools
- CNPD
- Gig Economy
- Emprego Público
- Public Sector Employment
- Contratação Pública
- Staff Costs
- Fiscal Law
- PPC
- Whistleblower
- Direito Civil
- Flextime
- Direito da Saúde
- Family Law
- Environmental Law
- Global Mobility
- ranikings
- Medicina Law
- pessoas coletivas
- M&A
- Proteção de
- international
- Laboral Law
- Public Employment Law
- Health Law and Social Security
- Labour and Social Security Law
- Electronic Invoice
- Tax Law
- Civil Law
- Commercial Law
- Public Contracts
- Electronic Invoicing
- Gender Equality
- Medical Error
- Forty Under Forty
- Self-Employed Workers
- Competition Law
- Employment Law
- Directory
- law firms
- Digital Era
- Global Business
- European Congress
- medical law
- Money Laundering
- Transparency
- Personal Data
- Minimum Wage
- Healthcare
- Secutity
- State
- Labour
- Sport Law
- Employment
- Partnership
- Chambers and Partners
- Public Employment
- Directories
- Business Law
- Students
- Trainees
- Administrative Law
- Administrative Litigation
- Guide
- conference
- Local Housing
- Public Procurement
- Health
- Innovation
- Data Protection
- Advertising
- Medicines
- Medical Devices
- Sports Law
- Real Estate
- Fairs
- Sports
- Guides
- Ranking
- Lawyers
- Magazine
- Law School
- Job
- Sport
- Press
- Women's Human Rights
- Women
- Human Rights
- Independent Workers
- Health and Life Sciences
- Health Law
- Chambers
- webinar
- Infarmed
- Helpo
- Workshop
- Football
- Iberian Lawyer
- Equality
- Man
- Woman
- Equal Pay
- Real Estate Law
- Immigration
- Foreign Investment
- Jornal Económico
- Marketing
- Chambers Europe
- In-Lex
- Emails
- Golden Visa
- traffic accident
- Team
- Labor Law
- Social Security
- Em
- Labour Code
- Family
- GRDP
- Research
- Clinical Research
- GDPR
- Children
- Industrial Property
- Social Security Law
- Europe
- Award
- Health and Scieces Law
- Labour Law
- Right of Preference
- Civil and Labour Litigation
- Local Accommodation
- Lawyer
- Social Responsability
Marco Real Martins nominated for the Forty Under Forty awards Read more
Take a step back and reassess your priorities Read more
Sports Law under analysis at the Faculty of Law of the University of Lisbon Read more
BAS presence in Expo Real 2016 Read more
BAS joins the Helpo sponsorship program Read more
National meeting on Public Contracts and Community Funds Read more
In 2019, there will be more changes in the contributory scheme for Independent Workers Read more
Advogar: BAS present at MIPIM Read more
Press: BAS reinforces its team with two new associate lawyers Read more
“Advocacy for Health Citizenship” Read more
BAS with three new trainee lawyers Read more
Exclusion of people from a football stadium Read more
Law Firm of the Year – Life Sciences Read more
Amendments introduced to the Labour Code Read more
Artur Filipe da Silva e Diogo Moreira Ramos author a chapter on real estate in Portugal Read more
BAS celebrates its 10th anniversary Read more
The impact of the new Data Protection Regulation on the Schools Read more
BAS lawyers in the Best Lawyers’ Global Business edition Read more
BAS represents the Portuguese jurisdiction in Employment & labour 2018 in the International Comparative Legal Guide Read more
Iberian Lawyer: “10 years of BAS Law Firm” Read more
General Data Protection Regulation and Health Data Read more
Award of public procurement Read more
Sports Law in 5 questions Read more
Margarida Ferreira discusses European legislation and its application in Portugal Read more
JM Seminar: Sports Law and Sports Policies Read more
António Gonilho joined the BAS team as a trainee lawyer Read more
BAS Portuguese Simplified Lay Off Guide at Iberian Lawyer Read more
Cláudia Monge speaks about medical secrecy and secrecy in law Read more
New regime of Article 256-A of the Public Procurement Code Read more
The recent changes in the assumption of multiannual liabilities by NHS entities Read more
BAS lawyers at EELA meeting Read more
BAS lawyers at the annual EELA meeting Read more
Key developments in the revised Public Procurement Code Read more
Iberian Lawyer Labour Awards 2024 finalists Read more
New BAS services: Immigration and Foreign Investment Read more
Press: Alexandra Almeida Mota practical talks about restructuring in Europe Read more
BAS in the Advocatus Search a Lawyer Guide Read more
BAS authors a chapter on Mozambique at ICLG Read more
BAS represents Portugal in EU Employment and Social Security Law Webinar Read more
BAS integrates business mission to Dubai Read more
Executive Program: “Contracting and Management of Public Works” Read more
Best Lawyers Distinguishes Pedro Madeira as Lawyer of the Year in Portugal Read more
Direct award and the re-enacting of prior consultation Read more
Funchal debates Public Procurement and Litigation Read more
“The role of Ethics Committees” Read more
BAS goes to college Read more
BAS lawyers distinguished by Leaders League Read more
Master of Sports Law Read more
BAS and real estate trends Read more
Smart work: The Law and the new trends in the labour market Read more
BAS strengthens its team with the arrival of Luciana Sousa Santos Read more
Public Procurement and Innovation Read more
Public Procurement and Pre-contractual Litigation under discussion: Analysis and evaluation of the proposals Read more
Data Protection: BAS joins APDPO Read more
General framework of the new GDPR and national law – Of medical data in particular Read more
Sports Law seen out of the box Read more
The draft law for a new Industrial Property Code Read more
2019 Highlights Read more
The consent of minors and the GDPR Read more
BAS ranked for Leaders League Best Firms in Portugal for Labor Law Read more
Updated Version: BAS Simplified Lay Off Guide Read more
III Health Law Course Read more
The changes in the Public Procurement Code Read more
Dália Cardadeiro wins Lawyer of the Year award Read more
Pedro Madeira de Brito speaker at the ILO centenary Read more
Summary of the ruling of the Supreme Administrative Court (First section) of 16.11.2017, case No 0935/17, rapporteur: Teresa de Sousa Read more
Partnerships for innovation, for what and how? Read more
EELA annual conference 2024 Read more
Team BAS reinforced Read more
BAS grows stronger with the arrival of Isabel Sousa Castro as associate lawyer Read more
BAS has welcomed two new Trainee Lawyers Read more
The new restrictions on loans of professional football players Read more
BAS at JobShop’23 Read more
Press: Employment Law Webinar Read more
BAS supports the 4th Public e-Procurement Congress Read more
BAS named Marco Aurélio as new partner Read more
Real Estate: BAS will be present at Expo Real in Munich Read more
Law firm ot the Year in Life Sciences Read more
BAS shortlisted for the Iberian Lawyer Labour Awards Read more
Information session on the changes to the Labour Code Read more
BAS is recognized in Data Protection by the Leaders League ranking Read more
Isabel Sousa Castro joins BAS team (Advogar) Read more
Smart work and the new trends on the labor sector Read more
BAS and Sports Law Read more
Cláudia Monge is a speaker at the Infarmed symposium Read more
BAS and Legalline Mozambique in Employment & Labour Law 2018 Read more
BAS at the European Employment Lawyers Association conference Read more
Comments to the Public Procurement Code Read more
Cláudia Monge wins “Lawyer of the Year” in Privacy and Data Security Law Read more
Press: BAS with five lawyers listed in Best Lawyers Read more
Chambers & Partners distinguishes BAS Read more
II Workshop – The National GDPR Enforcement Act: What to Expect? Read more
Five lawyers of BAS were recognized in Best Lawyers Read more
New sports law magazine Read more
Catholic University’s Law JobShop: BAS at the market of opportunities Read more
New general regulation for data protection Read more
BAS and the outcomes of MIPIM Read more
Sérvulo and BAS lawyers will debate about public procurement in Funchal Read more
BAS ranked in Chambers Europe 2020 Read more
Advogar: BAS distinguished with The Best Health Law Firm 2018 Award Read more
Advanced Training Programme on Public Procurement Read more
Green Hospitals Read more
BAS named the Best Health Law Firm 2018 Read more
IV Course in Health Law Read more
Forty under 40 finalists Read more
CELIA ALLIANCE publishes article from BAS about Portugal Read more
Catarina José focuses on the practical implications of GDPR Read more
COVID-19 – Exceptional Measures for Public Procurement and Expenditure Authorization Read more
ICLG: BAS writes about Labour and Employment Law in Portugal Read more
New rules for transparency in advertising Read more
Company Agreement under the microscope Read more
COVID-19: Exceptional and temporary Measures in Response to the Epidemiological Situation Read more
SB2020: Overall charges paid for service contracts Read more
Cláudia Monge will be a speaker at the conference on General Regulations for the Protection of Personal Data Read more
Rebenta a Bolha! (The game is over) Read more
BAS Agenda: 13th National Congress of Electronic Public Procurement Read more
Summer Internship Fair | FDUL Read more
What changes with the new Local Housing Law? Read more
The Women’s Human Rights Summit Read more
Who’s Who in Business Law in Portugal: Dalia Cardadeiro’s expectations for 2020 Read more
Cláudia Monge contributes to the book The Secrets in Law Read more
10 years, 10 partners, 10 stories: Marco Aurélio Constantino Read more
Priorities of the sector 2023 Read more
New Decree-Law no. 73/2021, of 18 August Read more
Local accommodation: will a global problem have a national solution? Read more
Portuguese companies at the Real Estate Show in Paris Read more
Preliminary consultation: the implementation of informality Read more
Cláudia Monge participates in a book celebrating the 40th anniversary of the NHS Read more
Football: The Right of Preference Read more
Read more
Catholic Porto analyses the impact of the processing of personal data Read more
BAS at Firm’s to Watch in The Legal 500 Read more
“Infarmed Conference – Use of data in health” Read more
BAS celebrates eight years Read more
BAS listed in the 15th edition of In-Lex Read more
Marco Real Martins reelected to the APMEP Read more
Video surveillance, GDPR Implementing Law and the Labour Code Read more
BAS organizes the workshop “Two years of General Data Protection Regulation. Are we ready?” Read more
Do you still receive advertising emails to which you did not give consent? Read more
Cláudia Monge analyses new data protection regulation Read more
Pedro Madeira de Brito distinguished by Best Lawyers Portugal 2017 Read more
Best Lawyers recognise BAS lawyers Read more
Pedro Madeira de Brito takes part in APODIT colloquium Read more
Public Health Policies in review Read more
Transparency in the advertising of medicinal products and medical devices Read more
BAS celebrates its ninth year Read more
The Employment Law team participate in the conference of EELA Read more
National Congress of Public Procurement Read more
Debate and book on Public Procurement Legal Framework Read more
Chambers Europe 2018 recognizes BAS partners in the area of Labor Law in Portugal Read more
Young lawyers and entry into the labor market Read more
Updating of Guaranteed Minimum Monthly Pay (“RMMG”) Read more
BAS at the Portuguese Real Estate and Tourism Show in Paris Read more
Pedro Madeira de Brito spotlighted in Life Sciences Read more
Paulo Pinto Pereira joins the BAS team Read more
Effects COVID-19: Extension of deadlines for implementation of electronic invoicing in public contracts Read more
Seminar “New Employment Relations” Read more
Developments in data protection and compliance can mean employment laws are quickly outdated Read more
Marco Constantino takes part in the Biennale of Jurisprudence in Medical Law Read more
Changes to the Labour Code Read more
Cláudia Monge opens workshop intended to review the first year of GDPR Read more
BAS and Cláudia Monge are finalists in Life Sciences at Iberian Lawyer Awards Read more
Press: Best Lawyers distinguishes Portuguese law firms and lawyers Read more
The framework of satellite clubs Read more
New minimum wage and update of service contract values Read more
GDPR and consent for scientific research Read more
Isabel Sousa Castro in the ranking Top 50 Iberian Lawyer Rising Stars Read more
BAS at the 20th anniversary of JobShop Read more
Clinical Research and GDPR: Are compromises possible? Read more
What has changed in the contribution regime for self-employed workers? Read more
Health: When data protection demands special attention Read more
Lessons in Portuguese Commercial Law by João Espírito Santo Read more
BAS in the 13th In-Lex Edition Read more
EELA Conference 2017 Read more
Pedro Madeira de Brito Publishes Book on Labour Law Read more
Advogar: BAS lawyers author a chapter on real estate in Portugal at ICLG Read more
COVID-19 – Support clients in times of mutual assistance of all and for all Read more
Real Estate Consulting Read more
Advocatus: BAS distinguished with The Best Health Law Firm 2018 Award Read more
How Portugal adopted the Real Estate Investment Trusts (REIT) regime Read more
The new Equal Remuneration Law under review Read more
Dália Cardadeiro in the Who is Who in Business Law in Portugal directory Read more
BAS debates restructuring processes in webinar on Labour Law Read more
JM Sports Seminar: Pedro Madeira de Brito opens afternoon session Read more
Cláudia Monge speaks at the Judicial Protection of Health as a Fundamental Right seminar Read more
Labour Law: changes to the Labour Code Read more
IBL Read more
“Whistleblowing” alerts for companies with 50 or more employees Read more
Marco Real Martins finalist in the Iberian Lawyer’s Forty under 40 Read more
BAS is a finalist in the Labour Awards Read more
Paris opens its doors in May to receive Portuguese real estate Read more
BAS in the 14th In-Lex Edition Read more
5th European Conference on Sustainable and Innovative Public Procurement Read more
Women in Law Read more
Decent Work Agenda Read more
Maísa Coutinho joins BAS Law Firm’s Read more
Healthcare security and State Civil Liability: imprisonment and mastery of guilt? Read more
Pedro Madeira de Brito participates in the new edition of the Annotated Labour Code 2020 Read more
The intriguing figure of the Data Protection Officer Read more
Life-long Learning One Health Read more
Real Estate Brochure Read more
BAS integrates two associate lawyers and a consultant, strengthening strategic areas and betting on new areas of expertise Read more
BAS in the Iberian Lawyer’s Lisbon Annual Report Read more
10 Key steps for compliance with the GDPR Read more
The exceptional and temporary regime for price revision and award Read more
BAS reinforces its team with three trainee lawyers Read more
FDUL provides courses in Law, Finance and Justice of Sport Read more
Cláudia Monge in a conference in Sintra on Medical Error Read more
General Regulation on Data Protection and the processing of personal data Read more
Sustainability and efficiency in the hospital sector Read more
Chambers and Partners recognizes BAS lawyers Read more
Summer Course on General Data Protection Regulation at the University of Lisbon School of Law Read more
Partner of BAS on the Best Lawyers’ directory Read more
Beneficiary Central Registry BCR Legal Regime – What are the obligations of a Company After the First Declaration Read more
Leaders League ranking recommends BAS in Labour Law Read more
Data Protection and Health Data Read more
BAS was present at Real Estate Fair in Paris Read more
50 Years of Law in Portugal Read more
Launch of the book “Civil Liability in Health” Read more
Labour Law team participates in the Congress of the ASNALA Read more
Registrations open for the workshop on GDPR implementation Read more
BAS on the directory Who’s Who in Business Law Read more
Advogar: BAS partners discuss Public Purchases in Health Read more
News from MIPIM 2019 Read more
Pedro Madeira de Brito co-authors the ‘Commentary on the European Convention on Human Rights and Additional Protocols’ Read more
Three BAS lawyers recognized in the Leaders League in the labour area Read more
Lauch of the book “Inventário Judicial” Read more
Postgraduate Course in Public Procurement Management Read more
Information session on the main changes to labour legislation Read more
BAS becomes a member of CELIA Alliance Read more
Lisbon 2020 – Work in a Digital Era – Legal Challenges Read more
Data Protection, Digital Security, and Compliance Course Read more
Claúdia Monge coordinates Medical Law course Read more
BAS at SIPP Read more
Processing data of children and young people in light of the new GDPR Read more
Cláudia Monge in debate with patient organisations “Hospital without walls” Read more
New legislation to fight against money laundering Read more
BAS ranked in Chambers Europe 2019 Read more
Data protection in Workshop Read more
The reform of the employment contract of sports practitioners Read more
Family Mediation Read more
Cláudia Monge at the “Dignity, Autonomy and Duration of Human Life” course Read more
BAS authors chapter on Labour Law in Portugal and Mozambique Read more
BAS joins business mission to Saudi Arabia Read more
Local Housing: Global Problem, National Solution? Read more
Course on “Health Law Read more
Alexandra Almeida Mota took part in the conference on Global Mobility Read more
BAS at the EELA annual conference Read more